
Trend Micro Cloud One - Workload Security : Protect your workload
Hi! Guys~
If you are looking for a third-party tool that can enhance the security of your workload on the cloud, I think this blog might give you the answer (or at least an idea for your option😉.)
Why do we need third party tools for security?
Doesn't AWS provide security tools for us? Why do we need more tools?
The answer is Yes.
AWS does provide security tools for us, however, Two main reasons why people need third-party tools like Trend Micro Cloud One - Workload Security are....
- To protect your workloads at all levels.
- To make it easy for your compliance management.
This tool comes in handy when you want more layers of protection and fully covered protection from network level to application level and want to stay compliant.
Trend Micro Cloud One - Workload Security provide comprehensive in-depth protection including anti-malware, application control, integrity monitoring, and more for your workloads.
This ensures that all layers of your cloud infrastructure are secured.
Besides, to help you stay compliant with least effort, Trend Micro Cloud One services also have features like Security Logs and Audit-Ready Reports, Compliance Templates.
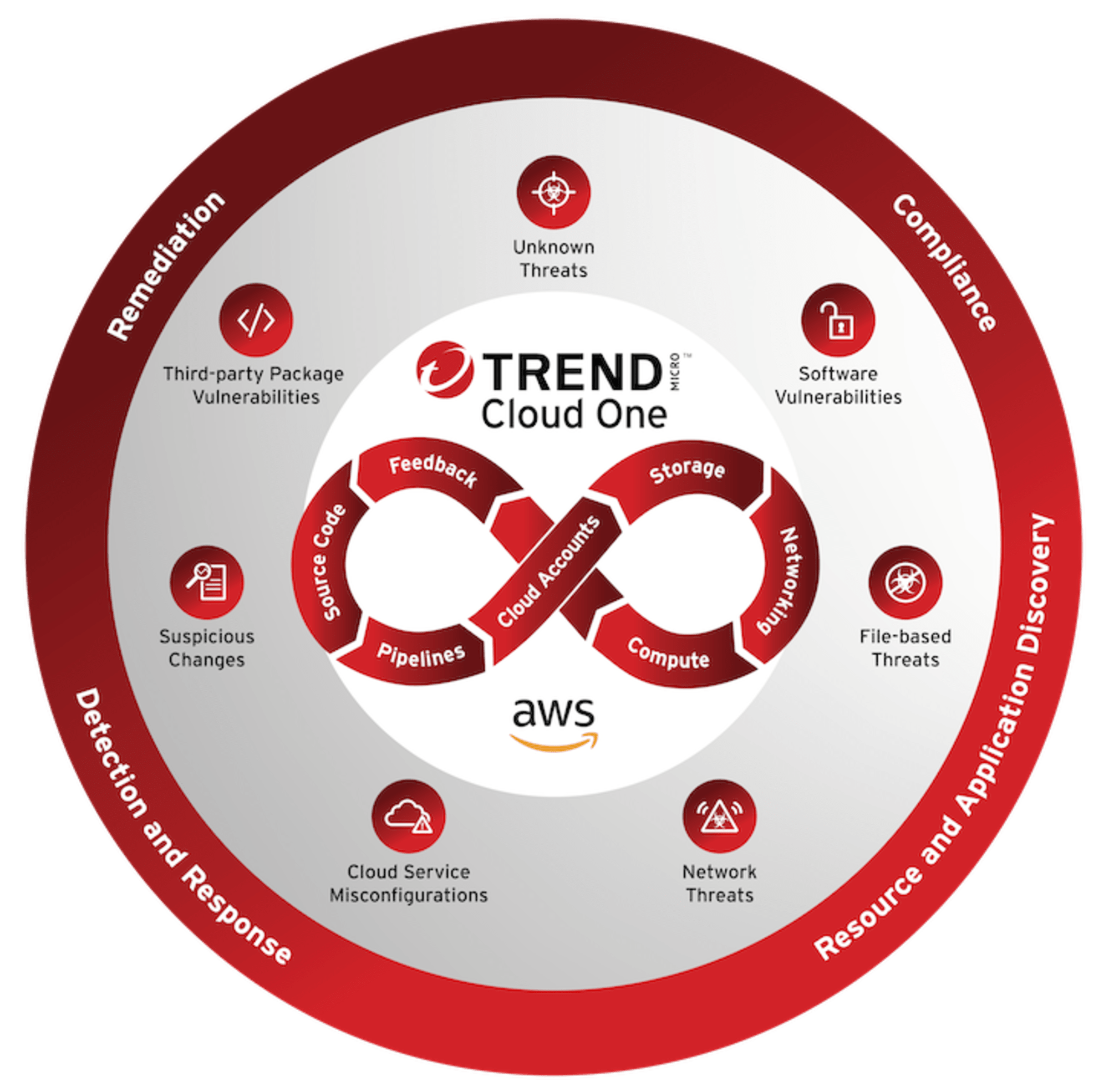
What is this blog about?
This blog aims to answer my own questions about ...
- What is Trend Micro Cloud One - Workload Security? Overview information to know this tool.
- How does it work? Does AWS offer any tool with the same feature and How is it different?
Here is the summary of what I have learned.
What is Trend Micro Cloud One - Workload Security?
I sometimes call it "Workload Security" for short.
It is one of services in the "Cloud One" series which is a set of cloud security services, from the company named "Trend Micro" which has developed various tools for different layers and dimensions of security to serve both on-premise and cloud usage.
"Cloud One" is the name of a platform or series designed specifically to protect workloads and infrastructure. Beside "Workload Security", they also offer Container Security ,File Storage Security ,Network Security and so on.
But today I want to focus on the service called Workload Security, as it's the tool to protect your Workloads including servers or EC2 instances which, I think, is a fundamental infrastructure for any application.
Workload Security provides real-time monitoring, intrusion detection for unauthorized access and malicious attacks, and advanced threat protection to secure your cloud environment.
The tool itself can be used in various environments, including cloud, on-premises, and hybrid setups.
Key Feature for Workload Security
Formerly known as Deep Security as a Service, Work Load security enhances multiple layers of security with these features.
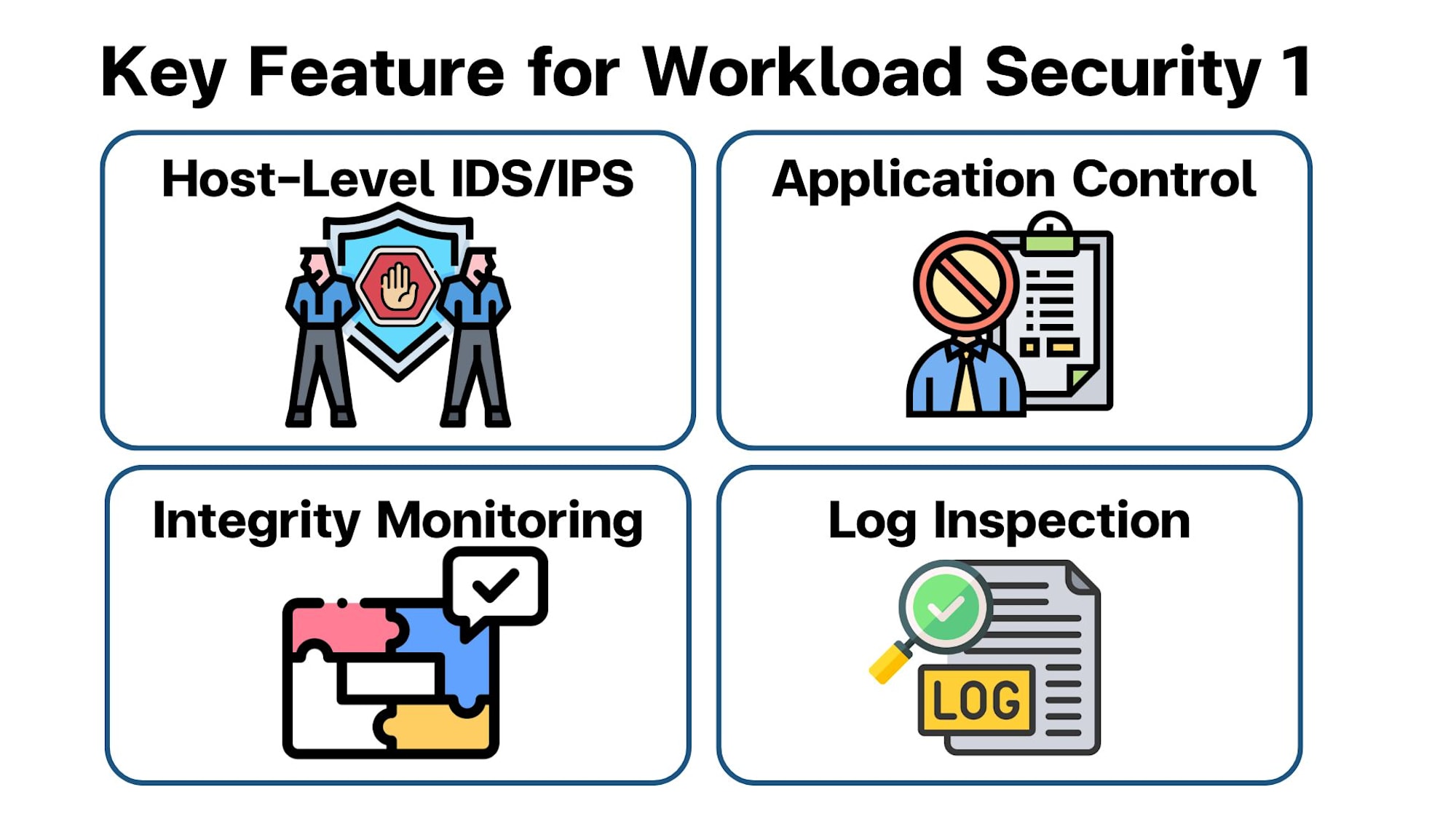
- Intrusion Detection and Prevention System (IDS/IPS) with Host-Level Protection
Workload Security includes a host-based Intrusion Detection and Prevention System (IDS/IPS) that scans traffic and application behaviors at the server or workload level. This feature helps prevent attacks that attempt to exploit vulnerabilities within your workload.
While AWS offers AWS Network Firewall and GuardDuty, which provide network-level intrusion detection, host-level IDS/IPS is not natively included in AWS. Trend Micro’s IDS/IPS goes deeper by protecting individual workloads (virtual machines, containers) from targeted attacks.
-
Application Control
Application Control within Workload Security ensures that only authorized applications can run on your workloads. You can create a whitelist or blacklist to prevent unauthorized or potentially malicious applications from executing.
In the shared responsible model of cloud AWS, you need to protect your workload in Cloud too. -
File and System Integrity Monitoring (FIM)
Workload Security provides Integrity Monitoring, which tracks changes in critical system files and configurations. If an unauthorized or unexpected change occurs, it triggers an alert, helping to detect breaches or malware that may be modifying system files.
While AWS Config can track some configuration changes and AWS Systems Manager offers monitoring capabilities, there is no built-in file and system integrity monitoring service as comprehensive as what Trend Micro offers. Integrity monitoring is essential for detecting subtle changes that might indicate a security breach.
- Log Inspection
Workload Security includes Log Inspection, which collects and analyzes security-related logs from your workloads. This helps identify suspicious activities, such as unauthorized access attempts or configuration changes, by correlating log data across different sources.
AWS provides CloudWatch Logs and AWS GuardDuty for log collection and threat detection, but detailed log inspection for workloads with pre-built security rules is a specialized feature that Workload Security provides.
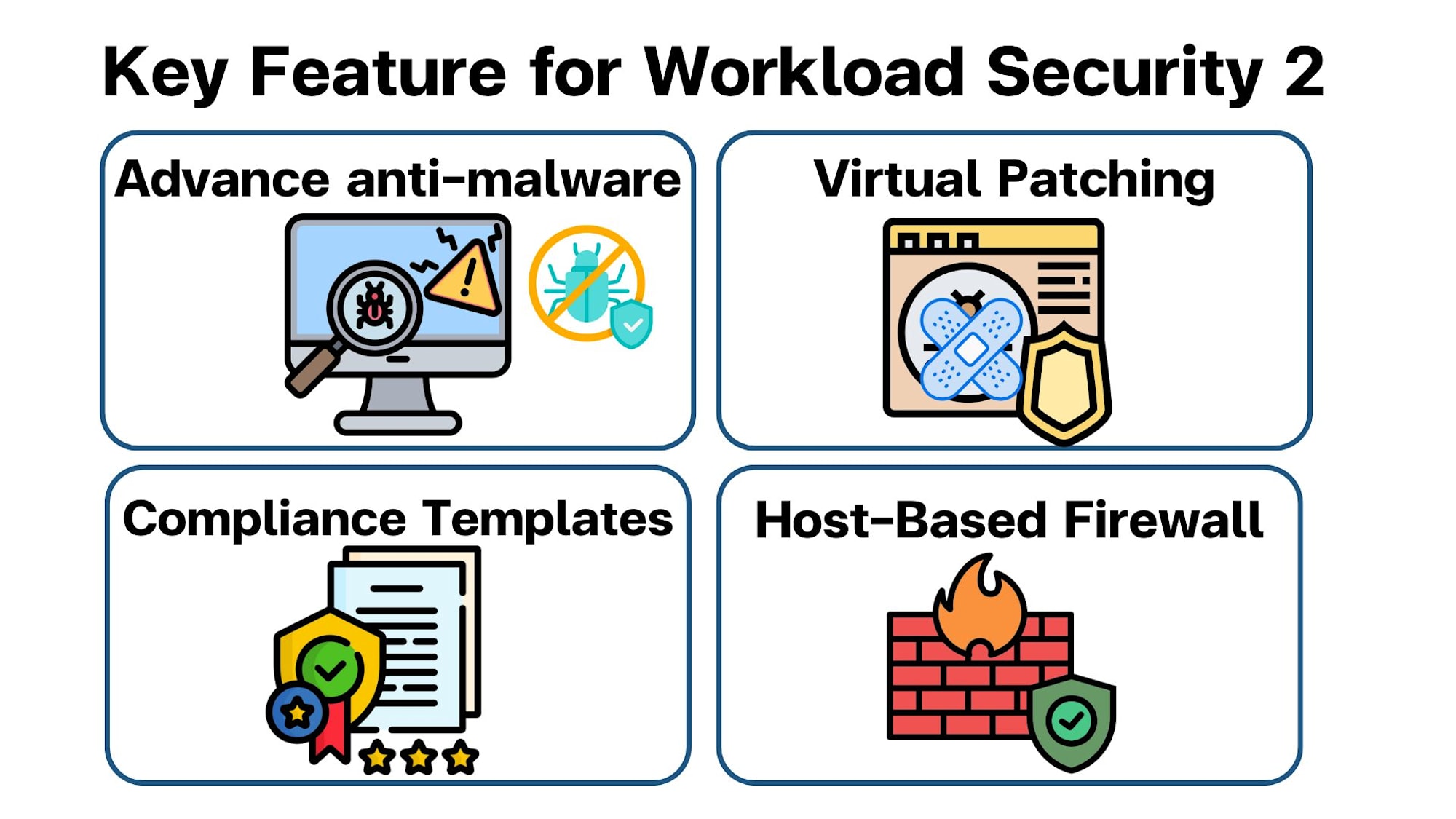
- Advanced Malware Detection and Protection
Workload Security includes anti-malware features that detect and block malware in real-time across workloads, virtual machines, and containers. It also offers advanced protection against ransomware, spyware, and zero-day threats.
AWS services such as GuardDuty focus on detecting suspicious activity, but there is no built-in AWS service for in-depth, host-level anti-malware scanning and remediation.
- Virtual Patching (Vulnerability Shielding)
Workload Security offers virtual patching, which protects systems from known vulnerabilities without needing to immediately apply software patches. This is crucial for legacy systems or applications where immediate patching may cause downtime or isn't possible.
AWS provides tools like AWS Systems Manager Patch Manager for automating traditional patching, but virtual patching isn’t available. Virtual patching shields vulnerabilities until actual patches can be deployed, which is a unique offering of Trend Micro.
-
Compliance Templates and Pre-Built Security Policies
Workload Security comes with predefined templates for industry-specific regulations (e.g., PCI-DSS, HIPAA, GDPR) to help you stay compliant with regulatory requirements. These templates automate the application of necessary security measures for compliant workloads. -
Host-Based Firewall
Workload Security includes a host-based firewall that allows you to control incoming and outgoing traffic at the workload level. You can define granular security policies for each server, container, or virtual machine.
AWS provides AWS Network Firewall and Security Groups for network-level control, but host-based firewalls specific to individual workloads are not natively offered. The host-based firewall in Workload Security adds an additional layer of defense at the workload level.
While AWS provides excellent security services, Trend Micro Cloud One - Workload Security adds advanced, host-level, and application-specific protection features that AWS does not natively offer. These include virtual patching, host-based IDS/IPS, application control, file integrity monitoring, and centralized multi-cloud security management, among others.
Combining AWS’s native tools with Trend Micro Workload Security gives you a more comprehensive and layered security strategy, especially in complex, multi-cloud, or hybrid environments.
Use case
1. Flowserve
Service Used: Trend Micro Cloud One – Workload Security and Cloud App Security.
Story: Flowserve, a company known for its flow control products, had a growing IT environment spread across multiple cloud platforms. They needed to secure this complex setup while moving most of their systems to the cloud. With Workload Security, they could protect everything from servers to operating systems against cyber threats like malware and ransomware. On top of that, Cloud App Security gave them extra protection for tools like Microsoft 365. A big bonus for them was virtual patching, which kept their legacy systems safe while waiting for updates—super handy!
2. Sandstone:
Service Used: Trend Micro Cloud One – Workload Security and Vision One.
Story: Sandstone, a property management and investment company, relied on Workload Security to safeguard their servers both in the cloud and on-premises, particularly from threats like ransomware. They also used Vision One for a more in-depth view of their environment, helping them quickly detect and respond to any security incidents. This helped them keep their sensitive data secure and ensured their operations ran smoothly.
AWS Marketplace and Pay-as-you-go benefit
When you use Trend Micro Cloud On in AWS, you can purchase it easily and conveniently in the AWS marketplace and pay based on how much you use.
On top of that, you get an additional 5% discount and support when you are Classmethod Members.
Special benefit for Classmethod Members
If your AWS account has already become Classmethod Members Service, you can purchase Trend Micro Cloud One - Workload Security and also other services in the series with a special plan called Solution Provider Private Offers (SPPO license).
With SPPO, you will get a special 5% discount and support (updated September 2024)
※ Classmethod Members Service has no initial or monthly fees and provides various benefits for your AWS accounts. Contact us for more details.
Furthermore, Classmethod has received the "TREND MICRO Partner Award 2023" and two of our engineers also received the "TREND MICRO Partner Engineer Award 2023"
Classmethod achieved the overwhelmingly No. 1 sales record for Cloud One on AWS Marketplace from April 2023 to March 2024.
In addition, we have had a huge impact on a wide range of areas, including publishing more than 20 articles about Cloud One and Trend Vision One each year on our Developers.IO blog web and promoting Cloud One as an essential third-party product for AWS native services through webinars.
If you are still unsure where to start, feel free to contact us.
References
Endpoint Security and Workload Security protection modules
Use case : Sandstone Technology
Use case : Flowserve
TREND MICRO Partner Award 2023 (Written in Japanese)



